2026 New capabilities announced
Avi Lamay
26/01/2026
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...
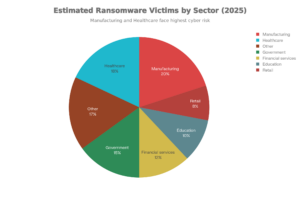
2025 in numbers
Hen Lamay
05/01/2026
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...
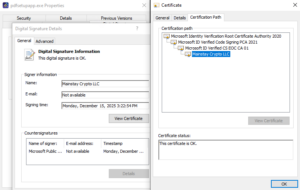
SparkOnSoft campaign continues and mutates
Avi Lamay
23/12/2025
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...
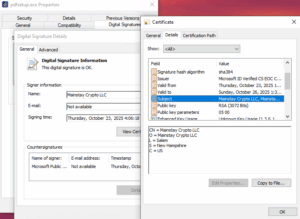
Case study – extinguishing SparkOnSoft malware
Avi Lamay
26/10/2025
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...

Winning the Cyber War Preventing Ransomware with Deceptive Solutions
Hen Lamay
10/07/2025
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...
Operation Midnight Hammer: Mastering Deception in Warfare and Cybersecurity
Hen Lamay
26/06/2025
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...

Deceptive Bytes mentioned in Gartner’s research on Top Use Cases in Preemptive Cyber Defense
Avi Lamay
18/11/2024
Receive high-fidelity alerts as threats are forced to uncover their presence when checking the environment prior to...
Lorem ipsum dolor sit amet, consectetur
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt
Lorem ipsum dolor sit amet, consectetur
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt