Intro
Yesterday (September 12th, 2024) our Active Endpoint Deception platform prevented a new variant of Malgent trojan horse that was built just a few hours prior to the attack on one of our customers in Latin America.
Entry Point
The user visited the website of a Mexican medical laboratory which is WordPress-based and was compromised, it displays a banner message to the user that a “Browser update required” (the banner didn’t appear at the time of publishing)
The user clicked on a link which was an AWS S3 hosted executable containing the malware itself and executed it from the browser.
Basic Information
The malware was made to look like a browser installation executable as the file’s attributes and properties indicate:
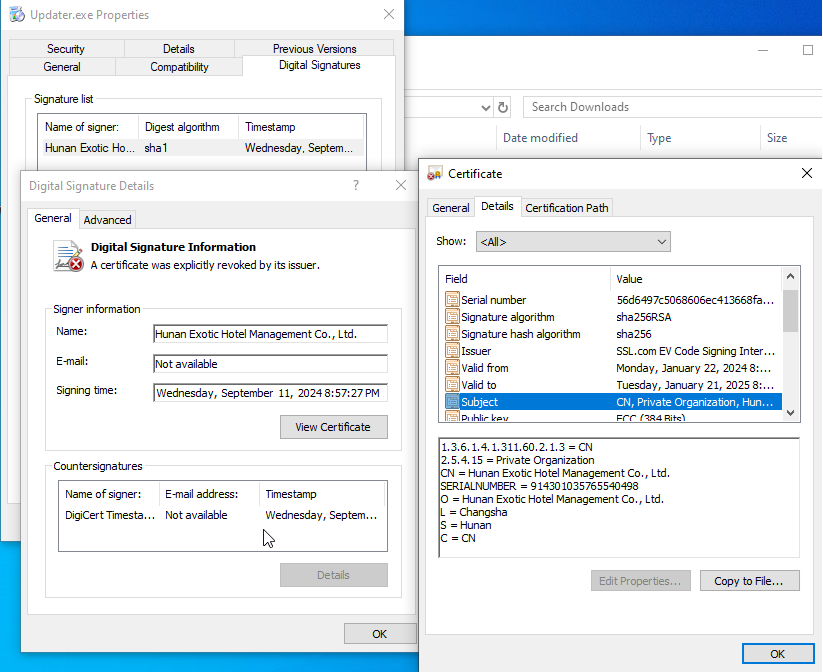
The file is signed by an Extended Validation certificate of a Chinese vendor to give the impression that the file is legitimate and safe (the certificate was not revoked at the time of the attack). Threat actors steal digital certificates and sign their files to evade detection and operate under reputable disguises
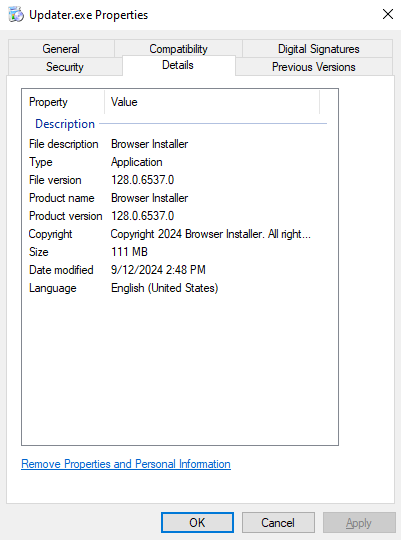
The file’s version is 128, indicating it likely mimicked Chrome or a Chromium-based browser (which is at the time of publishing at version 128 as well) and the file’s description, copyright and other executable properties suggest it’s a “Browser Installer” (without specific branding)
Also note that the file’s size is 111 MB, similar in size to Chrome’s offline installer. Large files are often used by attackers to bypass sandbox environments which are usually configured to run smaller files, even if the actual malicious payload is much smaller
Execution
When executed, the sample first checks if it’s running under WINE, a Windows compatibility-layer that allows Windows PE executables to run under Linux, macOS and other non-Windows operating systems, it does so by checking if the function wine_get_version exists in ntdll.dll, Windows’ Native API dynamic library

Prevention
Since the above execution is a clear indication of a malicious activity as attackers check for WINE to identify being investigated by security services utilizing WINE for malware analysis, the Deceptive Bytes platform immediately stopped the attack and the malware failed to infect the machine
IOCs
- SHA2: a12809c76461d00760bef767c98baf5909a4aed48f2256d3c42eb1ca62835c14
- Imphash: 55052bff3084bf220240d99b2216422e
- Certificate: Hunan Exotic Hotel Management Co., Ltd.
- Thumbprint: 9ad448726590d64e247266e0b6ff1524fa094a51
- Issuer: SSL.com EV Code Signing Intermediate CA RSA R3
- Root CA: SSL.com EV Root Certification Authority RSA R2
- Download URL: hxxps://bbuseruploads.s3.amazonaws[.]com/4c8dba68-b727-403e-8987-df9afd436402/downloads/7074f023-a845-467b-96a5-5cd3d3f69168/Updater.exe (no longer valid)
- Compromised website URL: hxxps://amlaboratorios[.]com
